With the explosive growth of IoT devices, security has become one of the biggest challenges in the development of IoT. This paper will delve into the infrastructure, major threats, protection strategies, and security standards of IoT security to help readers build a safe and reliable IoT system.
byword: IoT security, security architecture, threat modeling, cryptography, authentication, security standards
catalogs
1. Introduction
1.1 Importance and current status of IoT security
Internet of Things (IoT) technology is profoundly changing the way we live and work, with IoT devices being ubiquitous, from smart homes to industrial automation, from smart cities to smart healthcare. However, with the surge in the number of connected devices, the issue of IoT security is becoming increasingly prominent. Gartner predicts that by 2025, more than 75% of IoT projects will be delayed or fail due to security issues.
The importance of IoT security is reflected in the following aspects:
- Wide-ranging impact: IoT devices penetrate all areas of life, and security breaches can affect critical infrastructure, personal privacy and even personal safety
- Expanded attack surface: Every connected device can be an entry point for an attack, and the increase in the number of devices directly expands the attack surface
- cascade effect: In interconnected systems, a security breach in one device can lead to the collapse of the entire system
- Physical world impact: Unlike traditional IT systems, IoT security issues may directly affect the physical world (e.g., control systems being attacked)
- run: Many IoT devices are designed for long-term operation and require long-term security
The main issues facing IoT security today include:
- Limited equipment resources to implement complex security mechanisms
- Insufficient security awareness, many devices shipped with default passwords or no security protection
- Lack of harmonized standards and uneven security practices
- Inadequate updating mechanisms make it difficult to patch security holes in a timely manner
- Inadequate privacy protection and vulnerability of user data to unlawful collection and misuse
1.2 Special Challenges of IoT Security
IoT security faces a unique set of challenges compared to traditional IT security:
1.2.1 Technical challenges
- resource constraint: IoT devices typically have limited computing power, storage space and battery capacity to run complex security algorithms
- isomeric (chemistry): IoT systems contain a variety of different types of devices from different vendors, using different communication protocols and operating systems
- distributed deployment: Equipment is widely distributed and some deployed in physically difficult to protect environments
- long life cycle: Many IoT devices are designed to last up to 10-15 years, far longer than traditional IT equipment
- real time requirement: Many IoT applications require real-time response and security mechanisms cannot significantly increase latency
1.2.2 Management challenges
- Scale issues: Managing the security of tens or even hundreds of millions of devices
- Insufficient visibility: Difficult to fully monitor the security status of all equipment
- Difficulty in updating: Technical and logistical challenges to firmware and security updates for remote devices
- uncertainty of responsibility: Blurred boundaries of security responsibilities in a complex IoT ecosystem
- Lack of specialized knowledge: Cross-domain IoT security requires a combination of IT security and domain-specific knowledge
2. Internet of Things security threat model
2.1 Attack surface of IoT systems
The attack surface of an IoT system includes various aspects of the device, network, platform and application layers:
2.1.1 Device Layer Attack Surface
- physical interface: Debug interfaces such as UART, JTAG, SWD, etc. may be utilized to gain control of the device
- firmware: Firmware extraction, analysis and modification may result in security mechanisms being bypassed
- Hardware security: Side channel attacks, fault injection, etc. may break encryption keys
- transducers: Sensor spoofing and jamming can lead to incorrect decisions by the system
- local storage: Unencrypted sensitive data storage may be subject to unauthorized access
2.1.2 Network layer attack surface
- wireless communications: Signal jamming, man-in-the-middle attacks may undermine communications security
- communication protocol: Protocol Vulnerability Exploitation May Lead to Communication Hijacking
- network traffic: Traffic analysis and packet sniffing may reveal sensitive information
- Gateway equipment: Gateway Attacks and Hijacking Can Affect the Security of the Entire Network
2.1.3 Platform layer attack surface
- cloud service: API vulnerabilities, service misconfigurations could lead to massive data breaches
- data storage: Database vulnerabilities, unauthorized access may lead to theft of sensitive data
- identity management: Credential theft, elevated privileges may lead to system takeover
- service component: Dependent Component Vulnerability Could Be an Entry Point for Attacks
2.1.4 Application Layer Attack Surfaces
- web application: Traditional Web security issues (e.g., XSS, CSRF) may impact management interface security
- mobile application: Application reverse engineering, insecure data storage may leak user credentials
- user: Social Engineering Attacks May Induce Users to Perform Dangerous Actions
- business logic: Logic vulnerabilities and business process flaws may be exploited to bypass security controls
2.2 Common IoT Security Threats
2.2.1 Device Layer Threats
- firmware attack: Discover vulnerabilities by extracting and analyzing firmware to plant backdoors or malicious code
- physical attack: Access to sensitive information or control through physical access to equipment
- initiation process attack (IPA): Modify boot loader or boot process to implant malicious code
- hardware Trojan horse (computing): implantation of malicious hardware in manufacturing or supply chain processes for long term control
- resource exhaustion attack (REA): Consuming the device's limited computing, storage, or battery resources, resulting in denial of service
2.2.2 Network layer threats
- man-in-the-middle attack: Intercepts and potentially modifies communications between devices and servers to steal sensitive information
- denial-of-service attack: Make the network or device unavailable through a large number of requests, affecting the normal operation of the system
- replay attack: Capture and resend valid packets for unauthorized operations
- routing attack: Manipulate network routes to redirect traffic, enable traffic hijacking or listening
- slave network (used by spammers): Launching an attack by forming a large number of IoT devices into a botnet, such as the Mirai botnet
2.2.3 Platform and application layer threats
- Unauthorized access: Use weak authentication mechanisms to gain access to systems and control equipment or data
- data leak: Stealing or leaking sensitive data and violating user privacy
- API Abuse: Use of insecure API interfaces to enable unauthorized operations or data access
- malware: Specific malware targeting IoT platforms, such as ransomware or data-stealing tools
- privacy violation: Unauthorized collection and use of personal data in violation of users' right to privacy
3. IoT security infrastructure
3.1 Security architecture framework
A comprehensive IoT security architecture should cover all levels of devices, networks, platforms and applications, and throughout all stages of the device lifecycle:
Figure 2: IoT security architecture framework
3.1.1 Layered security architecture
Device Security Layer::
- Secure Boot and Firmware Validation - Ensure that only validated code can execute on the device
- Hardware Security Module (HSM) or Trusted Platform Module (TPM) - provides secure key storage and cryptographic operations
- Secure storage and encryption - protect sensitive data from unauthorized access
- Device Identity and Authentication - Ensure device identity is unique and verifiable
- Resource Segregation and Access Control - restricting access between different components
network security layer::
- Secure communication protocols - protect data transmission using encryption and authentication mechanisms
- Network Segmentation and Isolation - Segmenting the network into different security zones
- Traffic encryption - ensures confidentiality of data in transit
- Network Monitoring and Anomaly Detection - Identify and respond to suspicious network activity
- Firewall & Intrusion Prevention - Blocking Unauthorized Access and Malicious Traffic
Platform Security Layer::
- Cloud Platform Security Configuration - Configuring Cloud Services Following Security Best Practices
- API Security - Protecting Application Programming Interfaces from Misuse
- Data encryption and protection - securing stored data
- Identity and Access Management - Control access to users and services
- Security Audit & Logging - Record and analyze security-related events
application security layer::
- Secure Coding Practices - Follow secure coding standards and best practices
- Application authentication and authorization - authenticate users and control access rights
- Data Validation and Cleansing - Preventing Injection Attacks and Data Contamination
- User Privacy Protection - Protecting your personal data
- Security update mechanism - timely patching of security vulnerabilities
3.1.2 Horizontal security functions
In addition to a layered architecture, IoT security requires a number of security features that span the layers:
- identity management: Harmonized identity management across all layers to ensure trusted identities of devices, services and users
- Key Management: Secure key generation, distribution, storage and updating as the basis for encryption and authentication
- safety monitoring: Comprehensive security status monitoring and anomaly detection for timely detection of security issues
- risk management: Ongoing risk assessment and management, prioritizing and addressing high-risk issues
- compliance management: Ensure compliance with relevant regulations and standards, e.g. GDPR, CCPA, etc.
3.2 Equipment Safety Basis
3.2.1 Secure Boot and Trusted Execution
Secure Boot is the first line of defense for IoT device security, ensuring that only authenticated code can execute on the device:
Key technologies to achieve safe start include:
- invariable root trust (finance): usually based on encryption keys in hardware security modules or ROMs as the starting point of the chain of trust
- Digital Signature Verification: Use asymmetric encryption to verify the integrity of each boot phase and prevent unauthorized modifications
- metrics initiation: Record hash values of components during startup for remote attestation and integrity verification
- security update: Ensure the security of the firmware update process and prevent malicious firmware installations
3.2.2 Hardware security fundamentals
Hardware security is the foundation for building IoT security and consists of:
- Hardware Security Module (HSM): Provides secure key storage and encryption operations to prevent key disclosure
- Trusted Platform Module (TPM): Provides device identity and integrity protection and supports remote attestation
- Safety Elements (SE): Provide an isolated execution environment for sensitive operations to prevent software attacks
- Physical Unclonable Function (PUF): Generate unique device identifiers based on hardware characteristics that are difficult to replicate
- anti-tampering technology: detects and responds to physical tampering attempts, protecting the physical security of devices
3.2.3 Device Identity and Authentication
Every IoT device needs a unique and verifiable identity for network access and service access:
- device identifier: Ensure device identity uniqueness based on hardware unique IDs, certificates or tokens
- Equipment certificates: X.509 certificates are stored in a secure area and used for device authentication
- multi-factor authentication: Combine multiple factors for device authentication to improve security
- zero-trust model: Continuously validate device identity and behavior without assuming that any device is naturally trustworthy
3.3 Network security foundation
3.3.1 Secure communication protocols
IoT communication requires the use of secure protocols and mechanisms:
- TLS/DTLS: Provides encryption and authentication for TCP and UDP communications to secure data transmission
- Secure versions of IoT protocols: e.g. MQTT-TLS, CoAP-DTLS, adding security mechanisms to lightweight protocols
- end-to-end encryption: Ensure that data is protected throughout the transmission path against theft by intermediate nodes
- key negotiation: secure session key establishment mechanisms such as Diffie-Hellman key exchange
3.3.2 Network Segmentation and Isolation
Reducing the attack surface and limiting the spread of attacks through network segmentation:
- differential segment (math.): Divide the network into small security zones to limit lateral movement
- VLAN isolation: Reduce the attack surface by placing different types of devices in different VLANs
- East-west flow control: Limit horizontal communication between devices to prevent the spread of attacks
- software-defined boundary: Identity-based network access control for dynamic access policies
3.3.3 Network Monitoring and Defense
Continuously monitor network traffic to detect and respond to anomalous behavior:
- deep packet inspection: Analyze network traffic content to identify malicious loads
- behavioral analysis: Establishment of equipment communication baselines and detection of deviations to detect anomalous behavior
- Intrusion detection/defense systems: Identify and block attack attempts to secure your network
- honeypot technology: Trap attackers and analyze attack techniques to detect threats in advance
3.4 Platform and data security
3.4.1 Cloud platform security
IoT cloud platforms require comprehensive security:
- Safety Configuration: Configure cloud services following security best practices to avoid configuration errors
- access control: Fine-grained access control based on the principle of least privilege to limit the scope of permissions
- resource isolation: Strict isolation between tenants to prevent cross-tenant attacks
- safety monitoring: Continuous security status monitoring and alerts for timely detection of security issues
- compliance management: Compliance with relevant industry standards and regulations, such as ISO 27001, GDPR, etc.
3.4.2 Data security and privacy
Protecting sensitive data in IoT systems:
- Data classification: Disaggregate data according to sensitivity and implement differentiated protection
- data encryption: Encryption of data at rest, data in transit and data in use for comprehensive data security protection
- data minimization: Collect only the necessary data to reduce privacy risks
- Data anonymization: Remove or obfuscate personally identifiable information to protect user privacy
- Data Lifecycle Management: Full life-cycle management from creation to destruction to ensure secure data handling
4. IoT security implementation strategy
4.1 Safety design principles
4.1.1 Safety-first design
Incorporate safety considerations into every stage of product design:
- Threat modeling: Identify potential threats and risks
- security needs: Clear definition of security needs and objectives
- security architecture: Designing architectures to meet security needs
- secure encoding: Follow secure coding standards and best practices
- safety test: Comprehensive testing of security features and vulnerabilities
4.1.2 Defense-in-depth strategies
Multi-layered security measures are used:
- multilayered defense: Implement complementary security controls at different levels
- fail-safe: Ensure that the system remains secure in the event of a failure of security mechanisms
- least privilege: Grant only the minimum permissions necessary to complete the task
- Default security: the system default configuration should be secure
- Simplified design: Reduce complexity and risk of errors and vulnerabilities
4.2 Security life cycle management
4.2.1 Equipment life cycle security
Safety management throughout the entire life cycle of the device:
- Security Design and Development: Integrate security into the design and development process
- Safe Manufacturing: Protection against supply chain attacks and hardware tampering
- Security deployment: Initial configuration and activation of security
- security operation and maintenance (O&M): Continuous monitoring and security updates
- Safe decommissioning: Safe decommissioning and disposal of equipment
4.2.2 Vulnerability Management and Response
Effectively manage security breaches and incidents:
- vulnerability scan: Regular scanning of systems for vulnerabilities
- Vulnerability Disclosure Policy: Clear process for vulnerability reporting and handling
- Patch Management: Timely testing and deployment of security patches
- event response: Rapid response and handling of security incidents
- recovery plan: Develop and test a disaster recovery plan
4.3 Security updates and patch management
Security updates for IoT devices are key to maintaining long-term security:
- Secure update mechanism: Verify the source and completeness of updates
- incremental update: Reduce the amount of updated data and adapt to bandwidth constraints
- Rollback mechanism: Ability to rollback to a stable version if an update fails
- automatic update: Enabling automatic security updates where appropriate
- Long-term support: Long-term security support for long-life equipment
5. IoT security standards and best practices
5.1 Key security standards and frameworks
5.1.1 International standards
- ISO/IEC 27001: Information Security Management System
- ISO/IEC 27400 series: IoT Security and Privacy Guidelines
- NIST Cybersecurity Framework: Risk management framework
- ETSI TS 103 645: Consumer IoT Security Standards
- IEC 62443: Industrial automation and control systems cybersecurity
5.1.2 Industry standards
- GSMA IoT Security Guidelines: Mobile IoT Security
- OCF Security Specification: Open Connectivity Foundation Security Standards
- CSA IoT Security Controls: Cloud Security Alliance IoT Security Controls
- OWASP IoT Top 10: Top 10 Security Risks in the Internet of Things
5.1.3 Chinese standards
- GB/T 37044: Overall requirements for IoT security
- GB/T 37045: IoT Perception Layer Gateway Security Technical Requirements
- GB/T 37025: IoT data transmission security requirements
- GB/T 37024: Technical Requirements for the Security of IoT Sensing Terminal Applications
5.2 Industry Best Practices
5.2.1 Equipment Manufacturer Best Practices
- Implementation of the Security Development Lifecycle (SDL)
- Provide secure default configurations
- Enforcement of mandatory password policy
- Provide security update mechanism
- Implement secure boot and code signing
5.2.2 IoT Deployment Best Practices
- Conduct a comprehensive risk assessment
- Implementation of network segmentation and access control
- Establishment of equipment asset inventory and management
- Implement continuous monitoring and anomaly detection
- Develop a security incident response plan
6. Case study: building a secure smart home system
6.1 Smart Home Security Architecture
A smart home system is used as an example to show how to apply IoT security architecture:
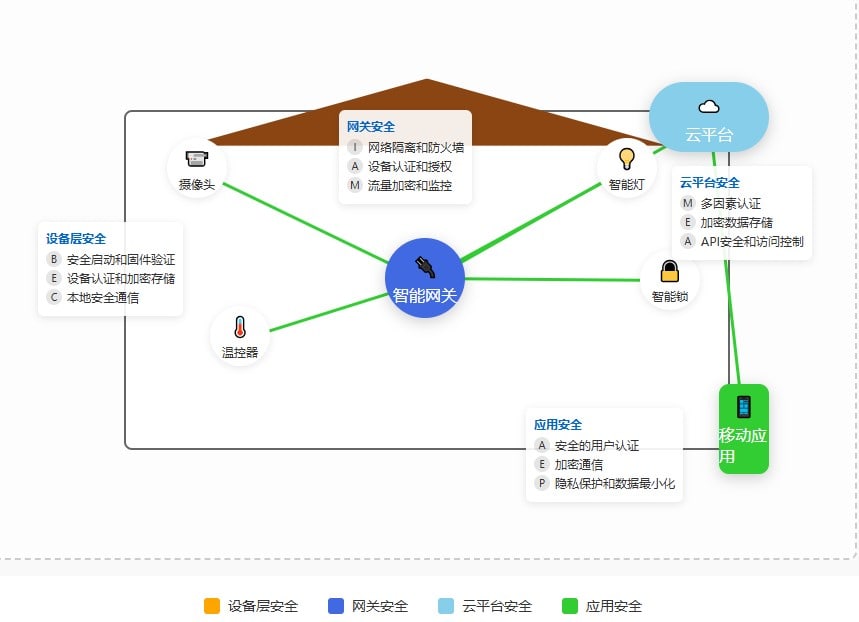
Figure 3: Smart Home Security Architecture
The security architecture of a smart home system includes:
- Device Layer Security::
- Secure Boot and Firmware Verification
- Device authentication and encrypted storage
- Local secure communications
- Gateway Security::
- Network isolation and firewalls
- Device certification and authorization
- Traffic encryption and monitoring
- Cloud Platform Security::
- multi-factor authentication
- Encrypted data storage
- API security and access control
- application security::
- Secure user authentication
- encrypted communications
- Privacy protection and data minimization
6.2 Security implementation points
Key points for the safe implementation of smart home systems:
- Equipment Selection: Select equipment and vendors with good security records
- network isolation: Separate smart devices from critical networks
- strong identification: Implement strong passwords and multi-factor authentication
- regular update: Keep all equipment and software up to date
- safety monitoring: Monitor device behavior and network traffic
- Privacy: Restrictions on data collection and sharing
6.3 Common Security Vulnerabilities and Protection
Common security vulnerabilities in smart home systems and their protection:
| Vulnerability Type | protective measure |
|---|---|
| weak password | Mandatory complex passwords, changed regularly |
| unencrypted communication | Encrypt all communications using TLS/DTLS |
| Unauthorized access | Implementation of multi-factor authentication and access control |
| firmware bug | Regular firmware updates, enable automatic updates |
| privacy breach | Data minimization, local handling of sensitive data |
7. Future trends and outlook
7.1 Emerging Security Technologies
Emerging Technologies in IoT Security:
- artificial intelligence (AI) security: AI-based threat detection and response
- Blockchain Security: distributed trust and device identity management
- quantum security: Encryption against the threat of quantum computing
- Autonomous security: Self-monitoring and self-healing security system
- Federal Learning: Distributed Machine Learning for Privacy Preservation
7.2 Security challenges and opportunities
Future Challenges and Opportunities for IoT Security:
- The scale challenge: Managing the security of billions of devices
- isomeric (chemistry): Harmonization of the security of different standards and technologies
- Long-term support: Continuous security support for long-life equipment
- new type of threat: Responding to evolving means of attack
- Regulatory Compliance: Adaptation to evolving safety regulations
8. Summary and recommendations
IoT security is a complex and evolving field that requires a combination of technology, process and people considerations. Building secure IoT systems requires:
- Adoption of a comprehensive security architecture covering device, network, platform and application levels
- Integrate security into every stage of design and development
- Implement a defense-in-depth strategy that does not rely on a single security control
- Continuous monitoring and updates to address evolving threats
- Adherence to industry standards and best practices
- Balancing security requirements with performance, cost and user experience
As IoT technology continues to evolve, security will continue to be one of the most critical considerations. Only an IoT system built on a solid security foundation can truly unlock its potential and gain the trust of its users.
bibliography
- NIST. (2023). NISTIR 8259: Foundational Cybersecurity Activities for IoT Device Manufacturers.
- ENISA. (2022). Guidelines for Securing the Internet of Things.
- ISO/IEC. (2021). ISO/IEC 27400: Information security, cybersecurity and privacy protection - IoT security and privacy guidelines.
- OWASP. (2022). OWASP Internet of Things Top 10.
- IEC. (2023). IEC 62443: Industrial communication networks - Network and system security.
- GSMA. (2022). IoT Security Guidelines.
- CSA. (2023). Security Guidance for IoT.
- China Academy of Information and Communication Research. (2022). Internet of Things Security White Paper.
- National Standardization Administration Committee. (2021). GB/T 37044-2021 Overall requirements for IoT security.
- Industrial Internet Industry Alliance. (2023). Industrial Internet Security Framework.
Content Reviewer: Josh Xu





